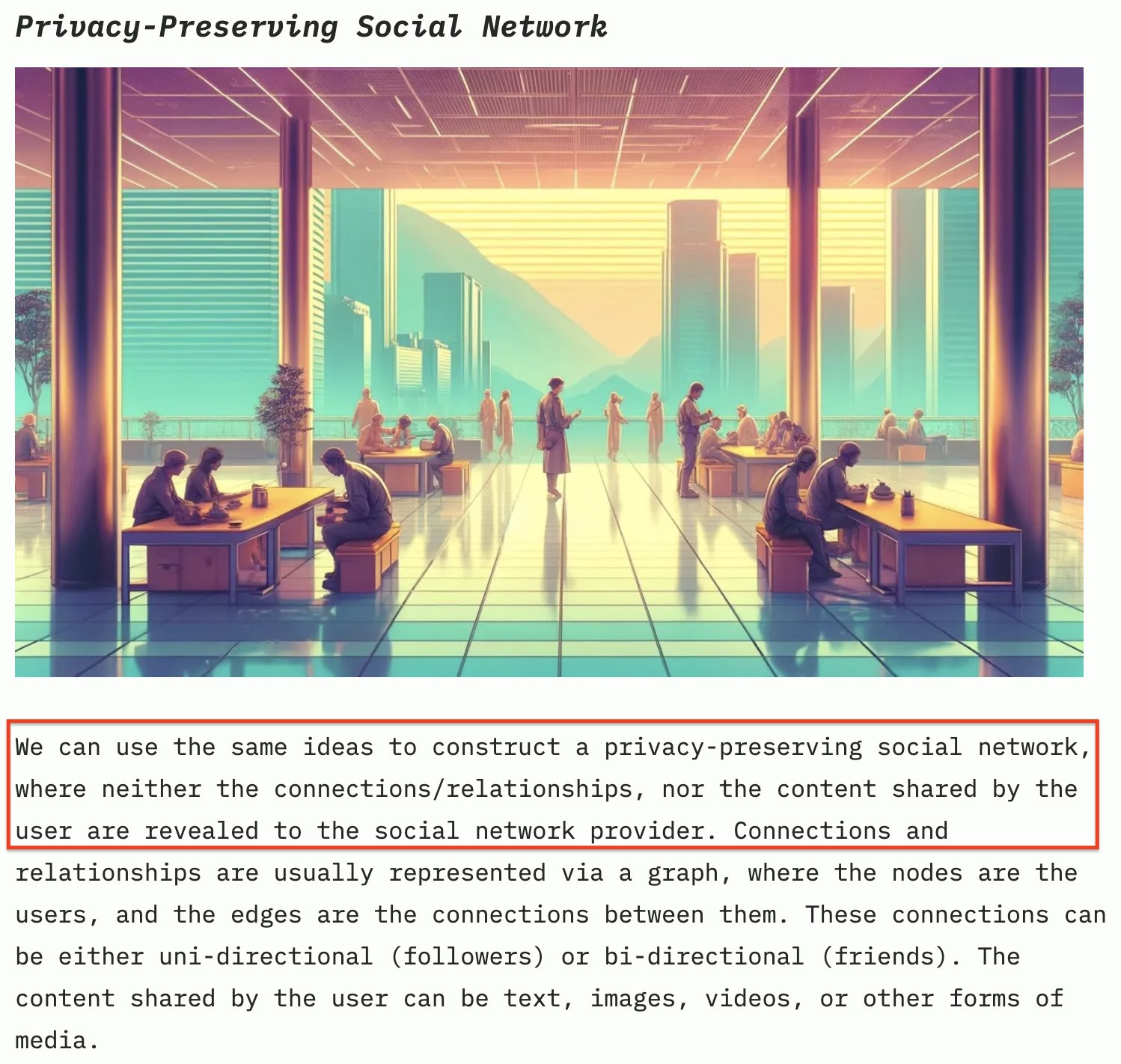
⬇️ My Thoughts ⬇️
🔍 The challenge with e-commerce privacy lies in two main areas:
1️⃣ Keeping search queries private 🔒
2️⃣ Protecting personal info like name and address 🙅♂️
Traditional platforms require us to trust them with this data

🛒 E-commerce & Privacy - Myth or Reality? 🔐
💻 Online shopping without revealing your personal data?
🚀 Zero-Knowledge Proofs (ZKP), zkLocus and Mina Protocol blockchain enable just that
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
Here's how 🧵👇
🛒 E-commerce & Privacy - Myth or Reality? 🔐
💻 Online shopping without revealing your personal data?
🚀 Zero-Knowledge Proofs (ZKP), zkLocus and Mina Protocol blockchain enable just that
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
Here's how 🧵👇
😳 ZKP will redefine what you know about computation and privacy
📍 This is what we are doing at zkLocus, by turning geolocation into a RWA
🔗 To learn more, visit https://zklocus.dev/

🪄 This is just one example of what is possible with ZeroKnowledge Proofs
📚 It was taken from my article "Privacy Is A Myth. Unless You're Using Zero-Knowledge Proofs" 👇
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
🪄 This is just one example of what is possible with ZeroKnowledge Proofs
📚 It was taken from my article "Privacy Is A Myth. Unless You're Using Zero-Knowledge Proofs" 👇
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/

🚨 By using Mina Protocol as a public layer for computation proofs, we create an auditable & transparent system 🕵️♀️
Anyone can verify that the cameras are operating as promised, without misusing the video data 🔍
🚨 By using Mina Protocol as a public layer for computation proofs, we create an auditable & transparent system 🕵️♀️
Anyone can verify that the cameras are operating as promised, without misusing the video data 🔍

📋 Here's how Mina Protocol blockchain fits into the picture:
1️⃣ zkSNARK circuits verifying camera code execution are stored on Mina
2️⃣ Commitments & ZKP circuits to the zkML model are also stored on the blockchain
3️⃣ All proofs from cameras are submitted & verified against them
📋 Here's how Mina Protocol blockchain fits into the picture:
1️⃣ zkSNARK circuits verifying camera code execution are stored on Mina
2️⃣ Commitments & ZKP circuits to the zkML model are also stored on the blockchain
3️⃣ All proofs from cameras are submitted & verified against them

🟣 Mina Protocol can implement the foundational layer 🚀
Verification keys that attest to the correct execution of the camera's code can be stored on $MINA 🔑
In practice, this involves commitments and ZKP circuits to the zkML model, thus ensuring the right one is used 🧠
🟣 Mina Protocol can implement the foundational layer 🚀
Verification keys that attest to the correct execution of the camera's code can be stored on $MINA 🔑
In practice, this involves commitments and ZKP circuits to the zkML model, thus ensuring the right one is used 🧠

🔐 zkSNARKs/zkSTARKs can be used to create ZK proofs that attest to the correct execution of the camera's code 📸
👮♀️ These proofs, representing an observation of a computation, ensure that non-suspicious video is discarded, thus preserving privacy
👉 Do not trust, verify 👈
🔐 zkSNARKs/zkSTARKs can be used to create ZK proofs that attest to the correct execution of the camera's code 📸
👮♀️ These proofs, representing an observation of a computation, ensure that non-suspicious video is discarded, thus preserving privacy
👉 Do not trust, verify 👈

🧩 Here's how a ZKP-powered surveillance system works:
1️⃣ Cameras feed live video into a zkML model
2️⃣ The model labels data as "suspicious" or "non-suspicious"
3️⃣ Only "suspicious" footage is stored & reported
4️⃣ The zkML model is public, ensuring transparency
🧩 Here's how a ZKP-powered surveillance system works:
1️⃣ Cameras feed live video into a zkML model
2️⃣ The model labels data as "suspicious" or "non-suspicious"
3️⃣ Only "suspicious" footage is stored & reported
4️⃣ The zkML model is public, ensuring transparency

🔍 The key lies in the verifiable computation model of Zero-Knowledge Proofs 🔑
Instead of trusting third-parties not to misuse data, we rely on cryptographic proofs to ensure privacy 💪
It's not about faith, but rather mathematical certainty 🧮
🔗 https://illya.sh/blog/posts/zksnark-zkstark-verifiable-computation-model-blockchain/
🔍 The key lies in the verifiable computation model of Zero-Knowledge Proofs 🔑
Instead of trusting third-parties not to misuse data, we rely on cryptographic proofs to ensure privacy 💪
It's not about faith, but rather mathematical certainty 🧮
🔗 https://illya.sh/blog/posts/zksnark-zkstark-verifiable-computation-model-blockchain/

📹 Imagine a global network of video cameras, monitoring every corner, every alley, even inside your home 🏠
Sounds like a privacy nightmare, right? 😨
Not necessarily! 😮
With ZKP, we can mathematically guarantee that private data is never stored or shared! 🔐
📹 Imagine a global network of video cameras, monitoring every corner, every alley, even inside your home 🏠
Sounds like a privacy nightmare, right? 😨
Not necessarily! 😮
With ZKP, we can mathematically guarantee that private data is never stored or shared! 🔐
🌍 Imagine 24/7 global video surveillance that doesn't compromise privacy
🤯 Sounds impossible?
😎 Zero-Knowledge Proofs disagree
Here's why 🧵👇
Linguistic vocal communication is such a wild concept 🤯
Like, I can take an abstract concept that I have in my mind, transform it into vibrations, transmit it wirelessly over air and have another individual parse it back into a similar abstract concept, now in their mind
👉 Learn more about ZKPs & privacy:
- zkLocus: https://zklocus.dev/
- zkSafeZones: https://zklocus.dev/zkSafeZones/
- Full article: https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
Let's make privacy the default, not an afterthought 🌟
🗣️ Privacy is a fundamental human right, and digital privacy is not an exception 📜
With Mina Protocol blockchain and ZKP solutions like zkLocus, we can build a future where privacy is the default 🙌
As the Web3 community, this is our mission & responsibility 💪

📹 Even 24/7 global video surveillance can be privacy-preserving with ZKP! 🌍
By combining zkML and verifiable computation, cameras can detect suspicious activity without storing private data 🕵️♀️
No, it's not magic. It's mathematics 🔐
📹 Even 24/7 global video surveillance can be privacy-preserving with ZKP! 🌍
By combining zkML and verifiable computation, cameras can detect suspicious activity without storing private data 🕵️♀️
No, it's not magic. It's mathematics 🔐
🔍 Imagine a search engine that never sees your raw queries, or a social network that keeps your connections hidden 😲
With ZKP, it's not just possible, but practical! 🎉
zkLocus, powered by Mina Protocol blockchain, is turning private geolocation into reality 📍

🌍 With ZKPs, we can build privacy-preserving: 🏗️
- Search engines 🔍
- Social networks 👥
- E-commerce platforms 🛒
- Even 24/7 global video surveillance! 📹
All without compromising functionality, business or individual privacy 💪
🌍 With ZKPs, we can build privacy-preserving: 🏗️
- Search engines 🔍
- Social networks 👥
- E-commerce platforms 🛒
- Even 24/7 global video surveillance! 📹
All without compromising functionality, business or individual privacy 💪

🔐 ZKPs remove the need to trust third parties for privacy. 🙅♂️
Instead, we rely on mathematical guarantees 🧮
This allows us to retain full custody & control over our data while enjoying digital services 😌
🔐 ZKPs remove the need to trust third parties for privacy. 🙅♂️
Instead, we rely on mathematical guarantees 🧮
This allows us to retain full custody & control over our data while enjoying digital services 😌

🌿 Merkle Trees, MPC, and homomorphic encryption complement ZKPs. 🍃
- Merkle Trees: Efficient & private data storage 📚
- MPC: Secure multi-party computation 🤝
- Homomorphic Encryption: Computation on encrypted data 🔒
🌿 Merkle Trees, MPC, and homomorphic encryption complement ZKPs. 🍃
- Merkle Trees: Efficient & private data storage 📚
- MPC: Secure multi-party computation 🤝
- Homomorphic Encryption: Computation on encrypted data 🔒

🔐 How does Mina Protocol blockchain fit into this? 🤔
$MINA serves as the foundation for ZKP apps, thanks to its programmable zkApps 🚀
It uses recursive zkSNARKs to create proofs of arbitrary computations, thus serving as the foundation of privacy solutions 💪
It's proof of everything
🔐 How does Mina Protocol blockchain fit into this? 🤔
$MINA serves as the foundation for ZKP apps, thanks to its programmable zkApps 🚀
It uses recursive zkSNARKs to create proofs of arbitrary computations, thus serving as the foundation of privacy solutions 💪
It's proof of everything

🔍 Solutions like zkLocus, zkSafeZones, zkML, and zkVM leverage ZKPs for privacy🛡️
- zkLocus: Private geolocation sharing on Mina Protocol blockchain 📍
- zkSafeZones: Civilian protection in warzones 🏥
- zkML: Private machine learning 🤖
- zkVM: Verifiable computation 💻
🔍 Solutions like zkLocus, zkSafeZones, zkML, and zkVM leverage ZKPs for privacy🛡️
- zkLocus: Private geolocation sharing on Mina Protocol blockchain 📍
- zkSafeZones: Civilian protection in warzones 🏥
- zkML: Private machine learning 🤖
- zkVM: Verifiable computation 💻
💡 Zero-Knowledge Proofs fix digital privacy 🌅
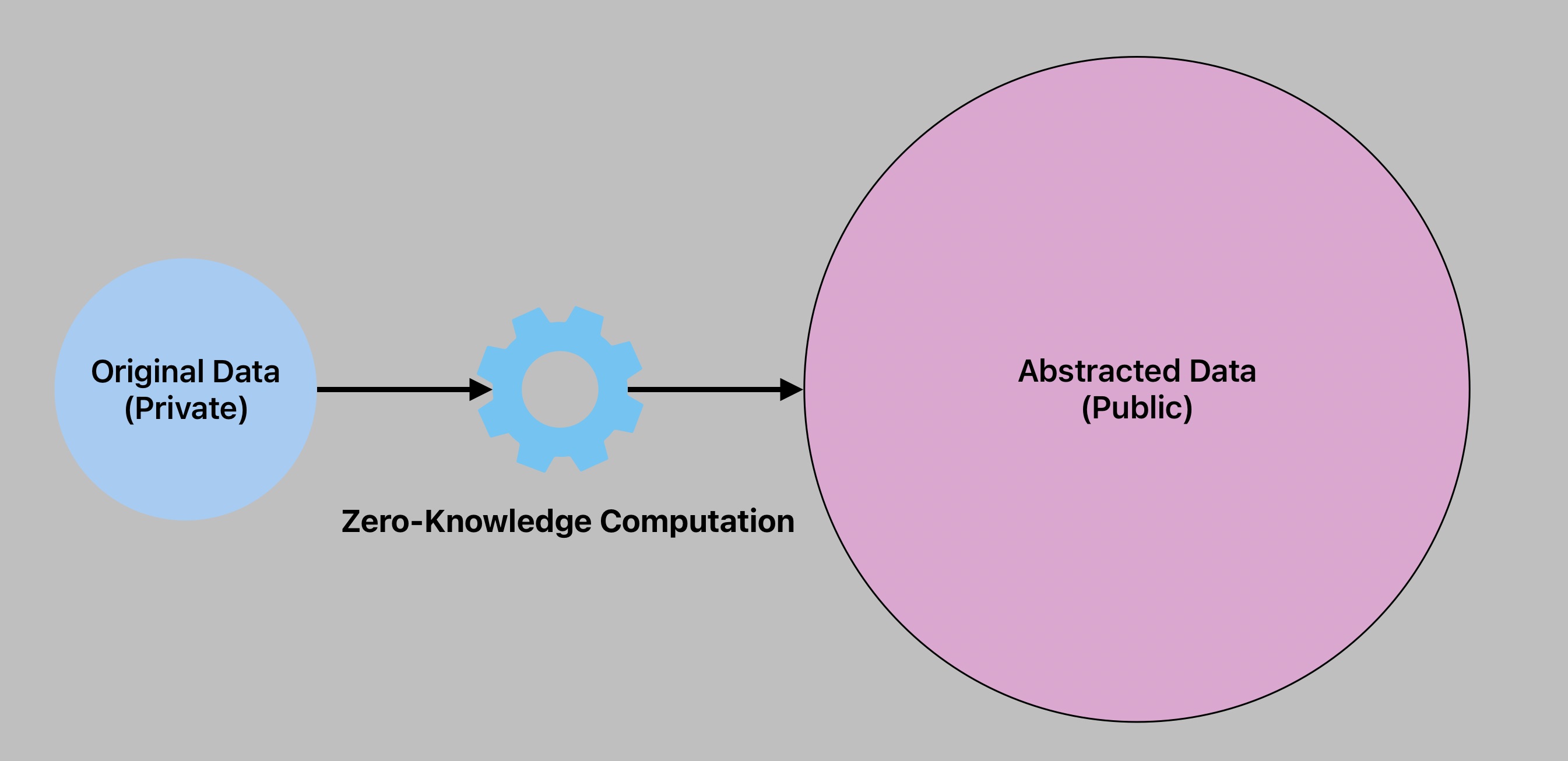
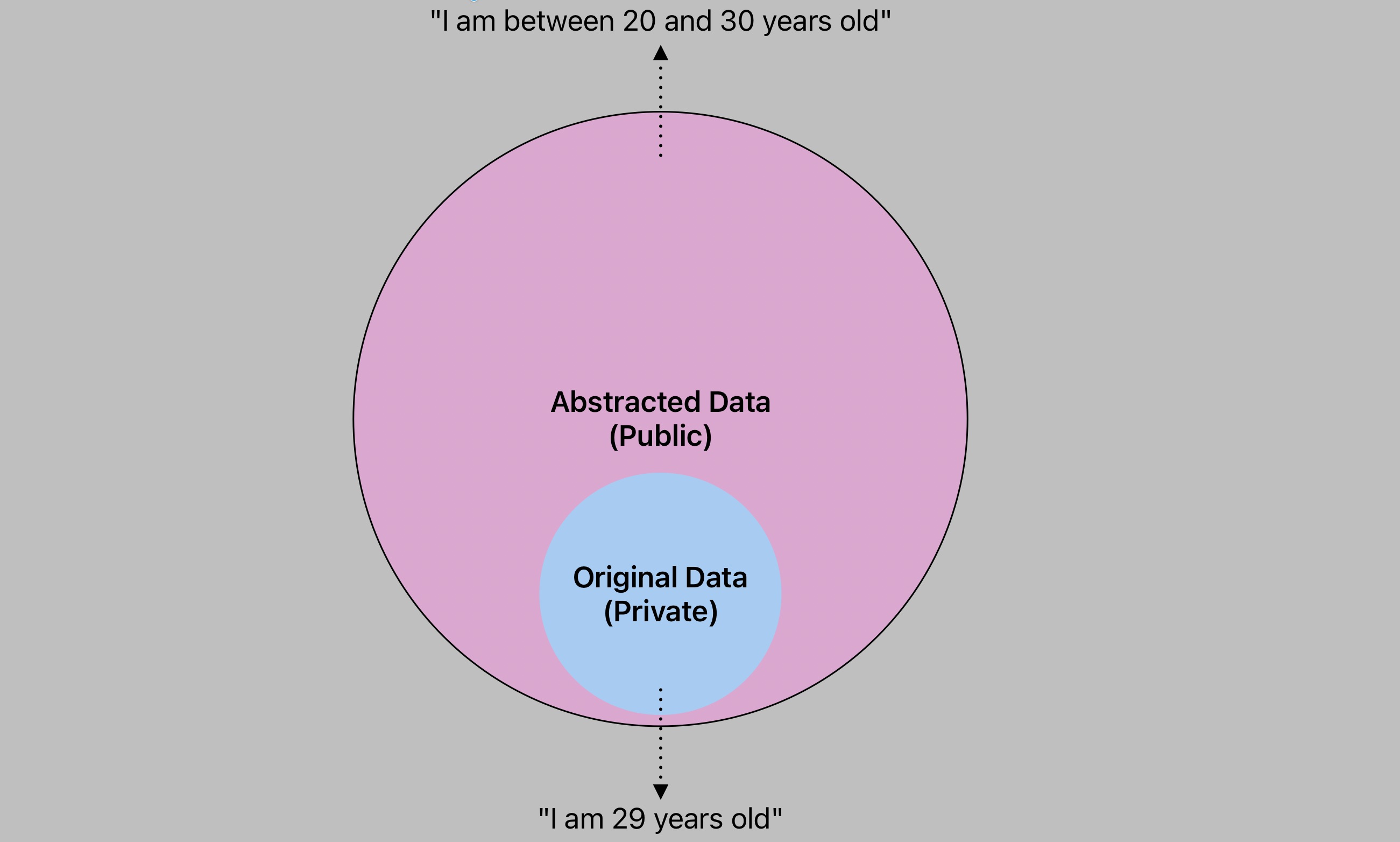
Instead of protecting sensitive data after sharing, ZKPs enable sharing data in an inherently private manner 🔐
By turning data into computation, ZKPs abstract it to preserve privacy 🧩
💡 The problem with digital privacy lies not in how data is stored & shared, but what data is shared 🤔
Even with encryption, once sensitive data leaves your device, it's compromised 😱
But what if we could share data in an inherently private manner? 🤯

🚨 PRIVACY IS A MYTH! 🕵️♂️
Digital privacy is fundamentally unfeasible, unless we rely on verifiable computation constructs like Zero-Knowledge Proofs (ZKP) 🔐
A thread 🧵 on why ZKPs are the key to true digital privacy 👇
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
Privacy ZeroKnowledge Web3
🚨 PRIVACY IS A MYTH! 🕵️♂️
Digital privacy is fundamentally unfeasible, unless we rely on verifiable computation constructs like Zero-Knowledge Proofs (ZKP) 🔐
A thread 🧵 on why ZKPs are the key to true digital privacy 👇
https://illya.sh/blog/posts/privacy-is-a-myth-without-zero-knowledge-proofs/
Privacy ZeroKnowledge Web3